As businesses continue the transition to supporting hybrid and remote workforces, they face the problem of managing the many devices that access enterprise resources. Employees must be able to communicate, work from any location, and access and connect to these resources securely. Administrators must safeguard business data, control end-user access, and provide user assistance from any site.
WHAT IS
Microsoft Intune
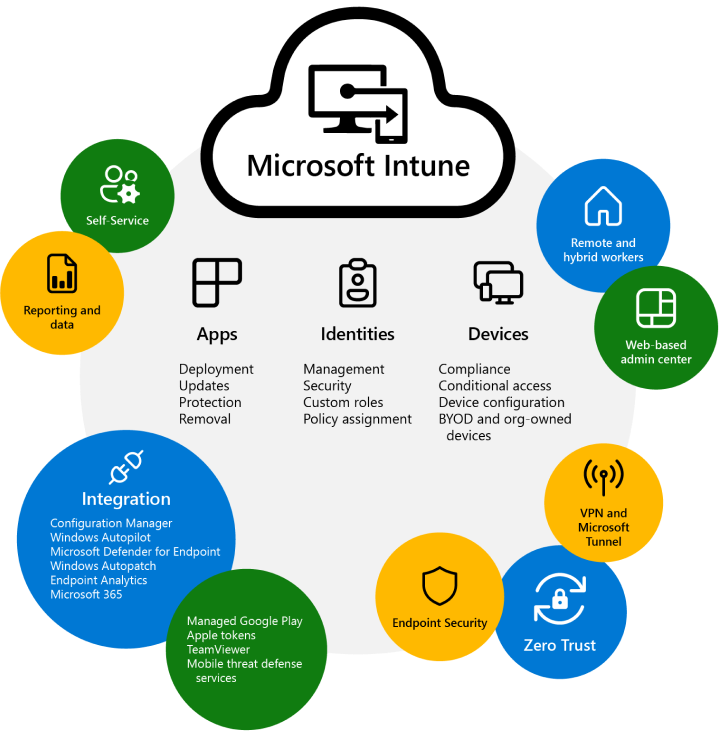
Microsoft Intune is a cloud-based system for managing endpoints. It streamlines app and device administration across all of your devices, including mobile devices, desktop PCs, and virtual endpoints, and governs user access. You can secure access and data on company-owned and user-owned devices. In addition, Intune’s compliance and reporting capabilities enable the Zero Trust security architecture. In Intune, you customise features and settings with rules that offer security and protection.
FOR
Organisation – Owned or BYOD Devices
There is simply no way around the fact that cybercrime is becoming more frequent and costlier.
Cyber attackers are constantly improving their ability to hack their way into a system that may appear to be protected.

You want complete control, particularly over security. When enrolled, devices get your security policies and configurations.On personal devices, consumers may not want IT administrators to have complete authority. To enable a hybrid workplace, provide people with alternatives. Intune can segregate company data from personal data. The objective is to secure your company’s information by regulating how people access and share data. For example, users must enrol their devices if they want full access to your organisation’s resources. Or, if these individuals just need access to Outlook or Microsoft Teams, implement app protection settings requiring multi-factor authentication (MFA).For mobile application management on personal devices in bring-your-own-device (BYOD) settings, you may utilise Intune (MAM). Because MAM is centred on the user, app data is safeguarded regardless of the device used to access it. There is an emphasis on applications, particularly safe app access and data protection inside apps.
THE
Key attributes and advantages
You can manage people and devices, including organisation-owned and personally-owned devices.
With an integrated app experience, Intune streamlines app administration, including app deployment, updates, and removal.
Intune automates the deployment of policies for applications, security, device configuration, compliance, and more. The sole need for devices to get these policies is internet connectivity.
Employees may utilise the Company Portal app’s self-service capabilities to reset a PIN/password, instal applications, and join groups, among other things. Customising the Company Portal app to decrease support calls is possible.
Intune incorporates mobile threat defence services, such as Microsoft Defender for Endpoint and third-party partner services. With these services, the emphasis is on endpoint security, and you can automate remediation and develop rules that react to attacks.
You use a web-based administration console that prioritises endpoint management and data-driven reporting. Administrators may access the Endpoint Manager admin centre from any internet-connected device.
Intune is compatible with other Microsoft services and applications
HOW INTUNE
Interfaces with other Microsoft products and services
Microsoft Intune interfaces with other Microsoft products and services that emphasise endpoint management, such as:
Windows Autopatch for automated Windows patching, Microsoft 365 applications for business, Microsoft Edge, and Microsoft Teams.

Microsoft 365 for productivity of end users Office applications, including as Outlook, Teams, Sharepoint, and OneDrive. Using Intune, you can deploy Microsoft 365 applications to organisation users and devices. You may also deploy these applications when users initially log in.

In Intune, a service-to-service link may be established between Intune and Microsoft Defender for Endpoint. You may define rules that scan files, identify dangers, and send threat levels to Microsoft Defender for Endpoint when they are connected. Additionally, you may build compliance procedures that establish an acceptable amount of risk. In conjunction with conditional access, you may restrict access to organisation resources for noncompliant devices.

Configuration Manager for on-premises endpoint management and Windows Server, including software update deployment and data centre administration.

Endpoint analytics provides visibility and reporting on end-user experiences, including device performance and reliability.

Windows Autopilot for contemporary OS deployment and provisioning.
Contact Us
Get In Touch With Us
If you are searching for a proven way to accelerate your business and provide a higher level of customer service, contact us for more information about the Jeeves.Plus instant messaging service.
